1. Create or Access Your Account
To get started, you need to:- Create an account: If you don’t already have one, follow the instructions in the account creation and first login guide.
- Log in: If you already have an account, sign in with your credentials at app.aegister.com.
2. Verify Your Virtual CISO License
After logging in, check that the Virtual CISO license is activated for your Organization. Only with an active license can you access the specific Virtual CISO services.
To obtain a license, please contact us.\
3. Navigating the “Cyber Assurance” Section
Once your license is confirmed, go to the Cyber Assurance section. Here you will find two main services:- Cyber Posture: Displays the current status of security policy implementation or compliance standards. Check it out here.\
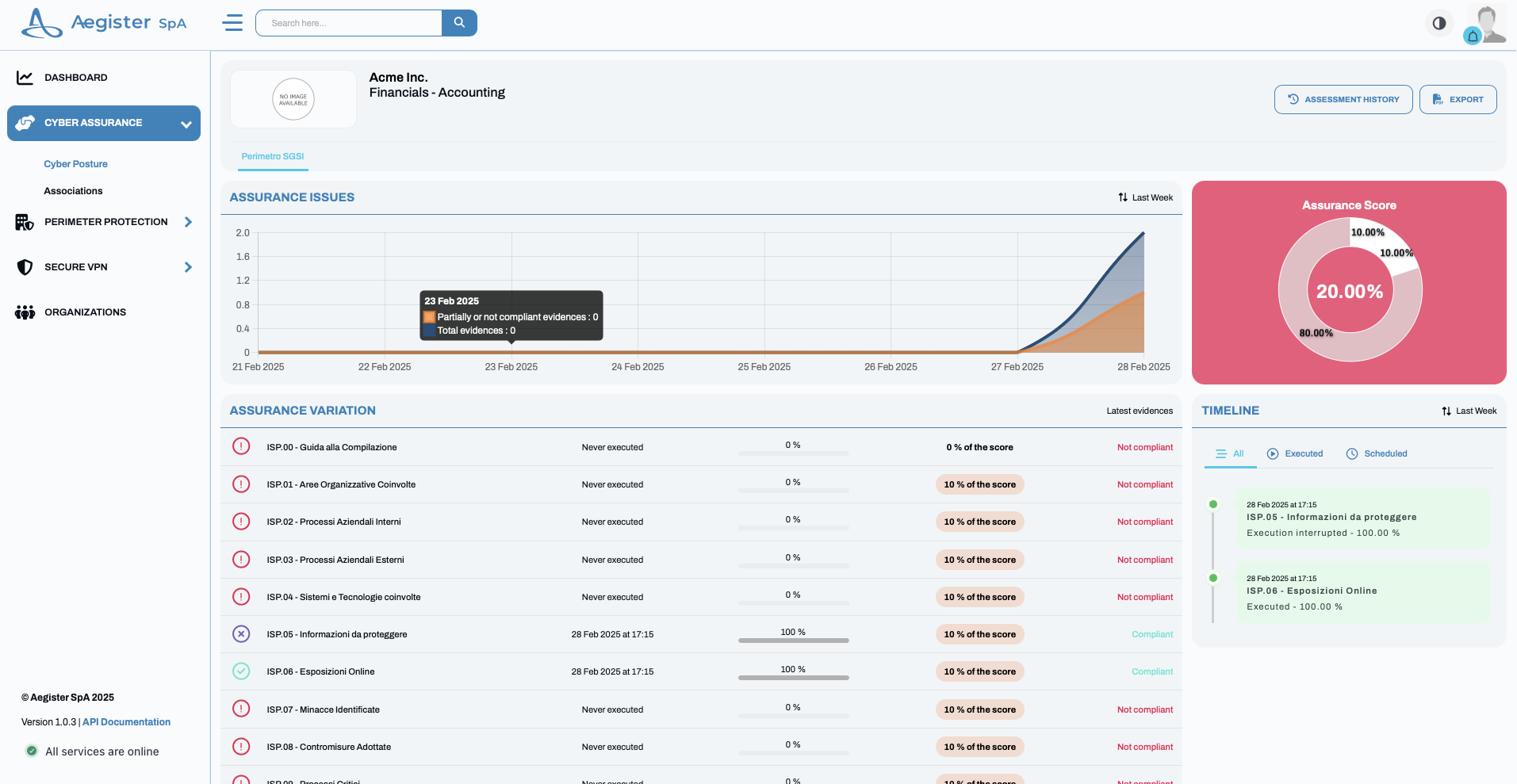
- Association: The service that allows you to add new security frameworks and complete the required tasks. Learn more in the Cyber Association section.\
4. Structure of the Cyber Assurance Section
The Cyber Assurance section is divided into two subsections:4.1 Cyber Posture
- Audience: Available to all users within an organization.
- Functionality: Displays the implementation status of the security activities outlined in the security frameworks associated with your organization.
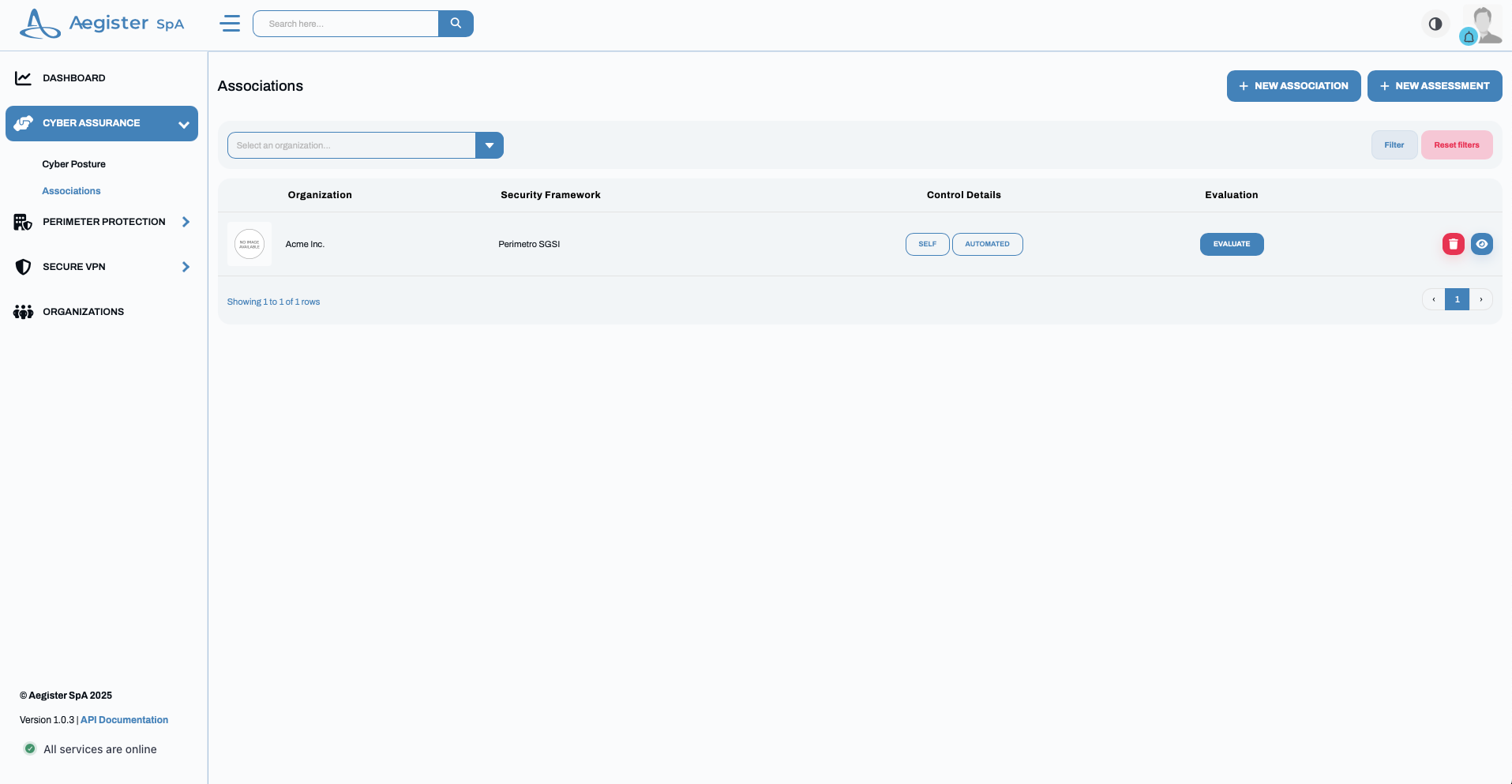
4.2 Association
- Audience: Reserved for security officers and owners.
- Functionality:
- Shows the security frameworks that Aegister has added to your organization.
- Allows you to independently add new security frameworks (tailored by Aegister to meet your specific needs).\
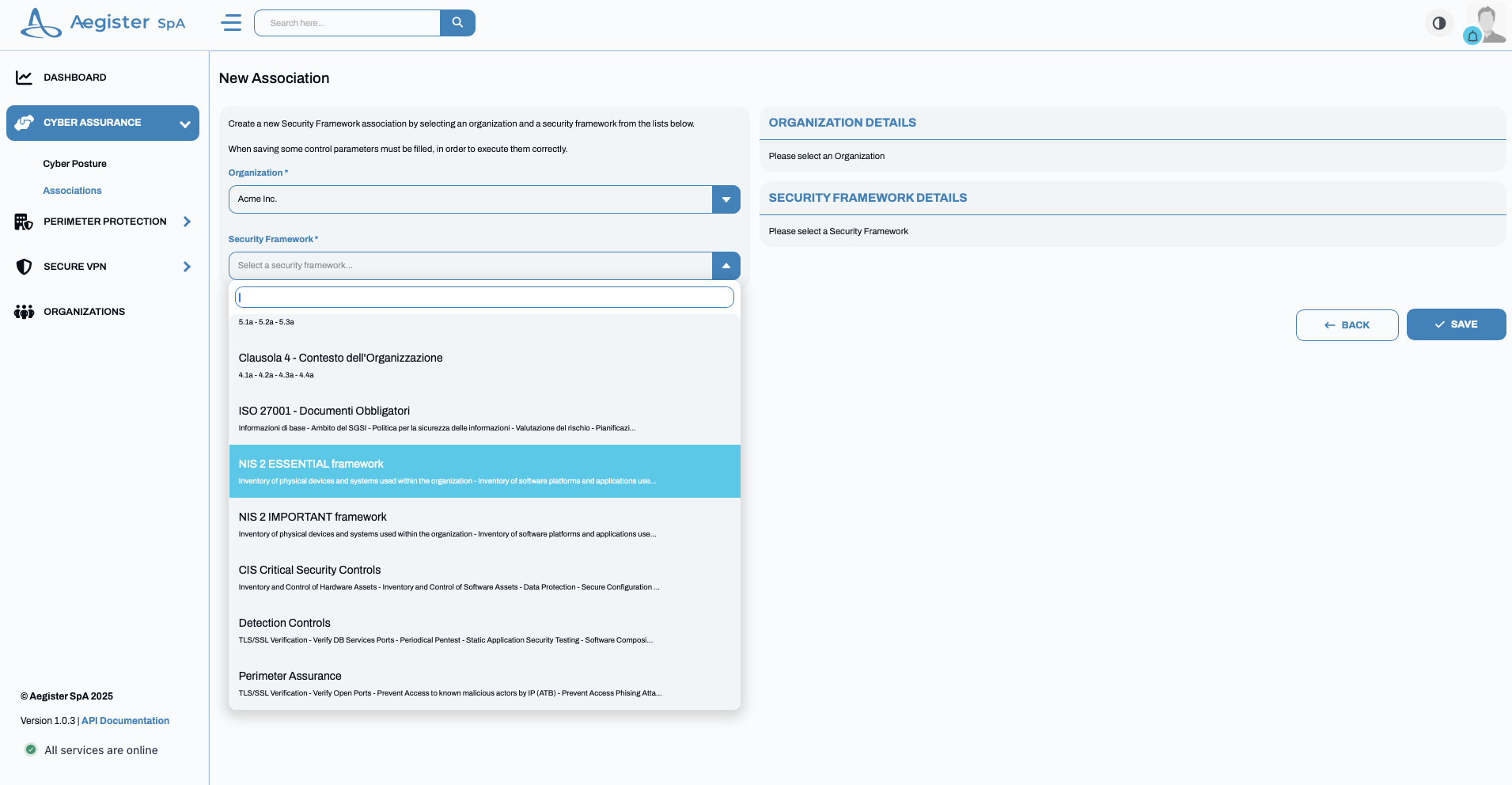
- Initiates the implementation of the necessary remediation tasks.
5. Task Management
Tasks are categorized as follows:- Automated: Scheduled scripts defined in the security framework that run periodically, with a log available to review past executions.
- Self: Tasks that require manual intervention.\
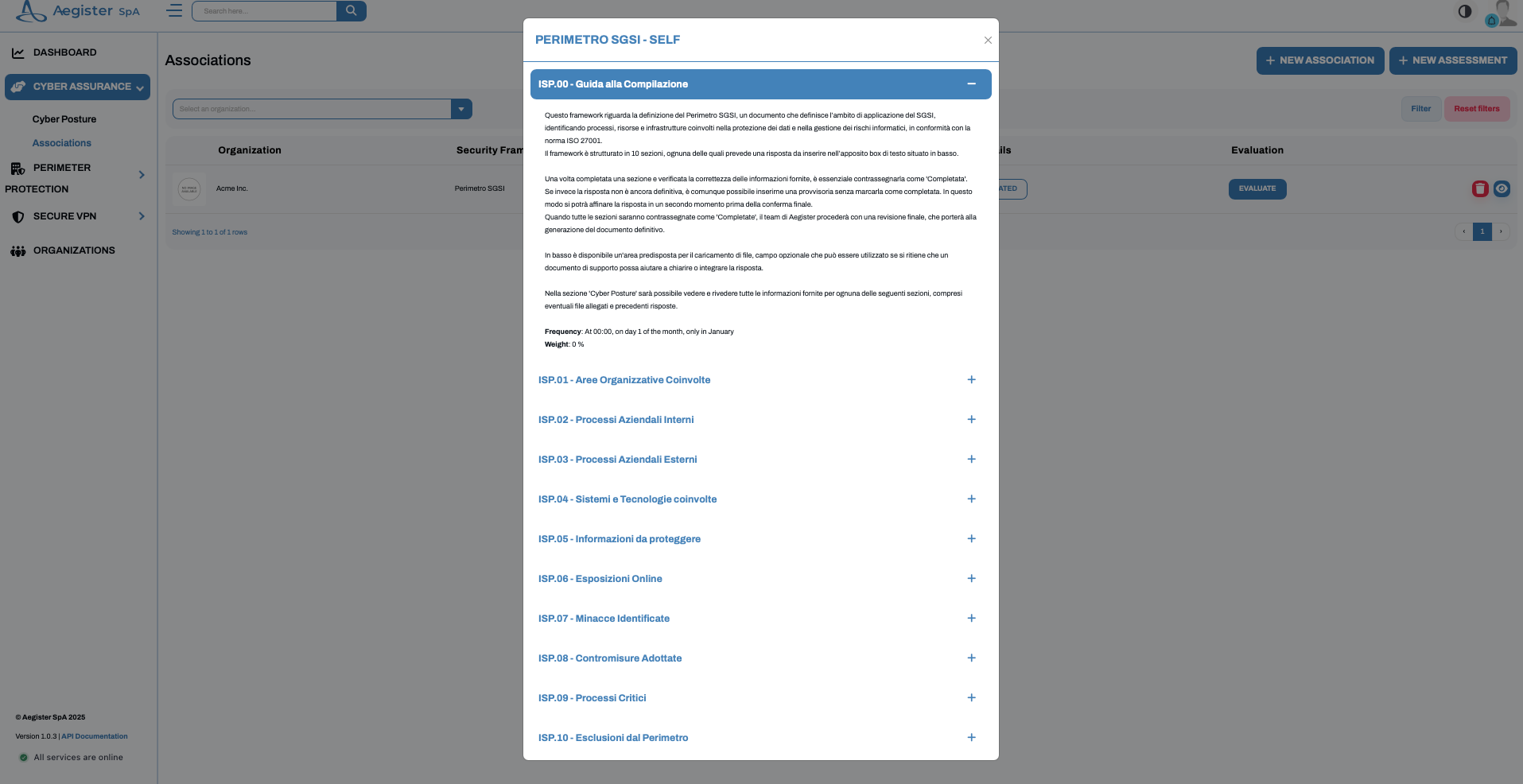
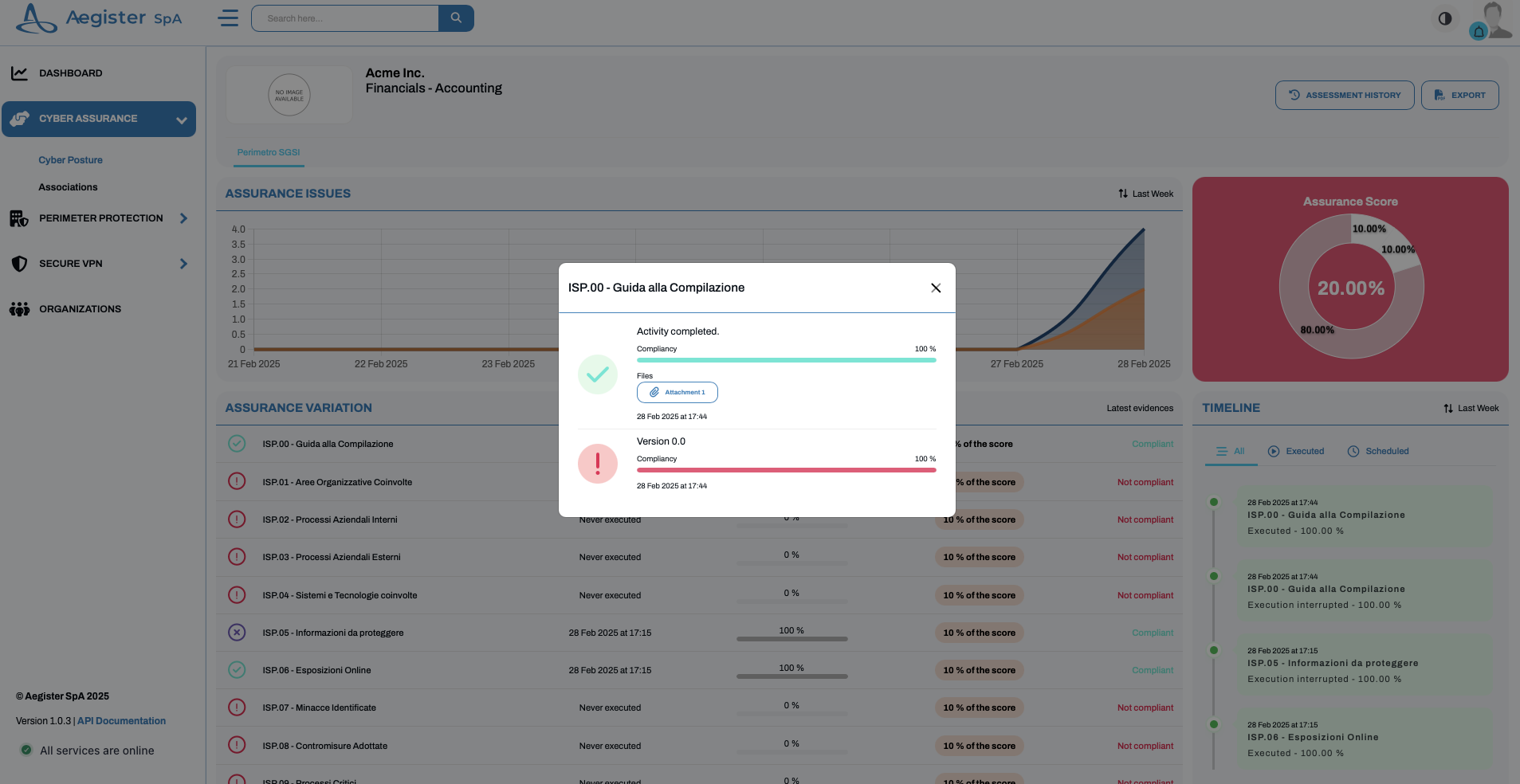
Task Evaluation and Documentation
- Evaluate: By clicking on “evaluate” within a framework, you can begin answering the assessment questions.\
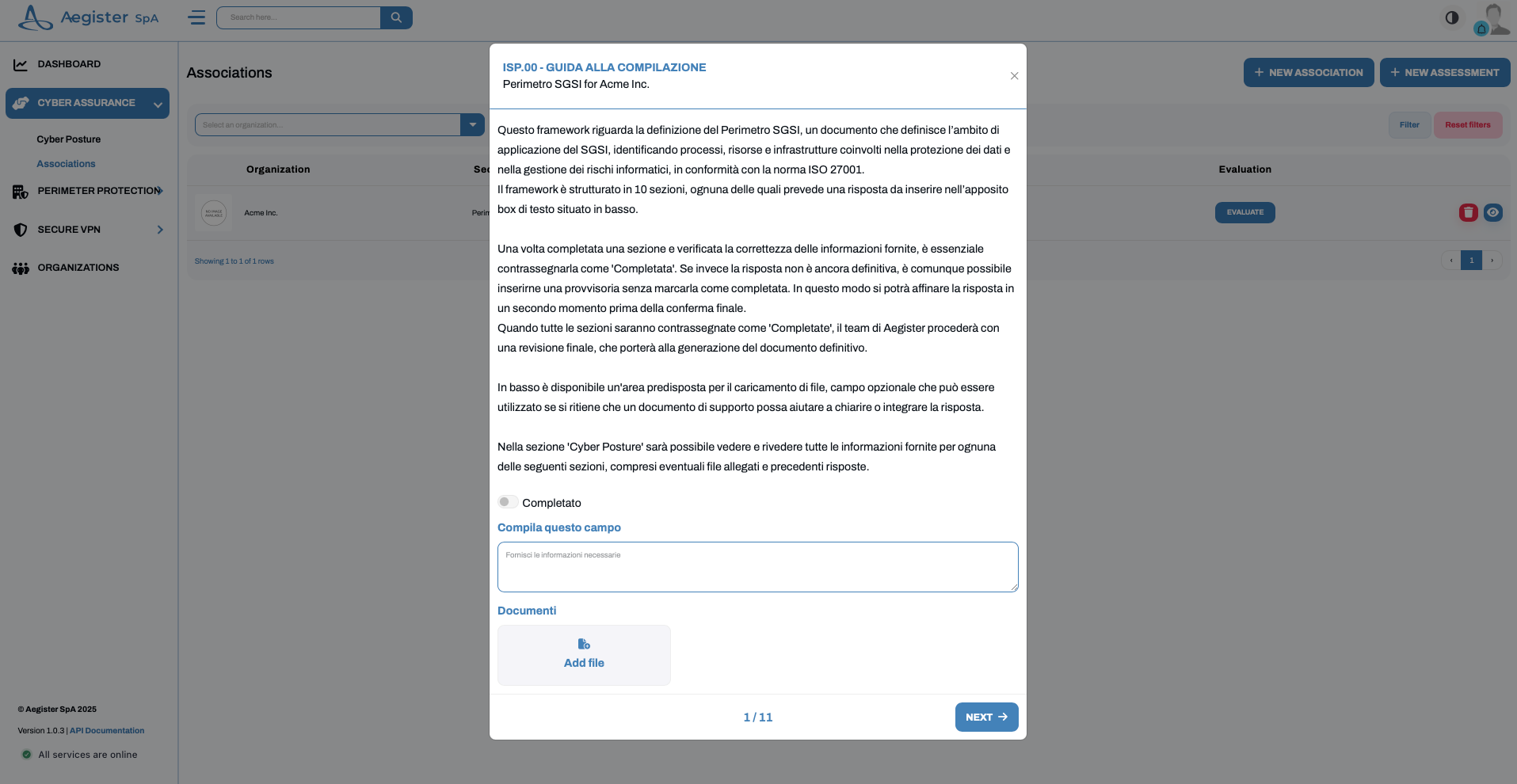
- Attachments and Completion: You can attach files as evidence or click “completed” to mark a task as finished.
- Versioning: In the Cyber Posture section, you can view the version history of responses and attachments, allowing you to track the evolution of your implementation.\