1. Corporate Account Creation
-
Preliminary:
Before proceeding, create an account for your organization on the Aegister Cyber Console. This step is essential for managing and monitoring the ATB device. Note: For devices pre-configured by Aegister for Partners, the organization has already been created. You can register directly on the platform here using a corporate account by registering your email and password, or by using SSO. Once registered, request the necessary permissions from your Aegister contact to access the ATB dashboard.
2. Physical Connection of the Device
-
Network Connection:
Physically connect the ATB device to your firewall using any available Ethernet port (LAN1-4). -
Connection Confirmation:
Once the device is connected, our team will receive a notification and begin the final remote configuration phase.
3. Technical Checks and Initial Configuration (by Aegister)
-
ATB–Cyber Console Connection Check:
The Aegister team will verify that the ATB is properly communicating with the Cyber Console. -
Aegister VPN Functionality Test:
The team will confirm that the integrated VPN tunnel is operating correctly, ensuring remote access for maintenance and updates. -
ATB Local IP Verification:
Access the ATB section of your Aegister Cyber Console to verify that the ATB is connected and to view its PUBLIC_IP and LOCAL_IP.\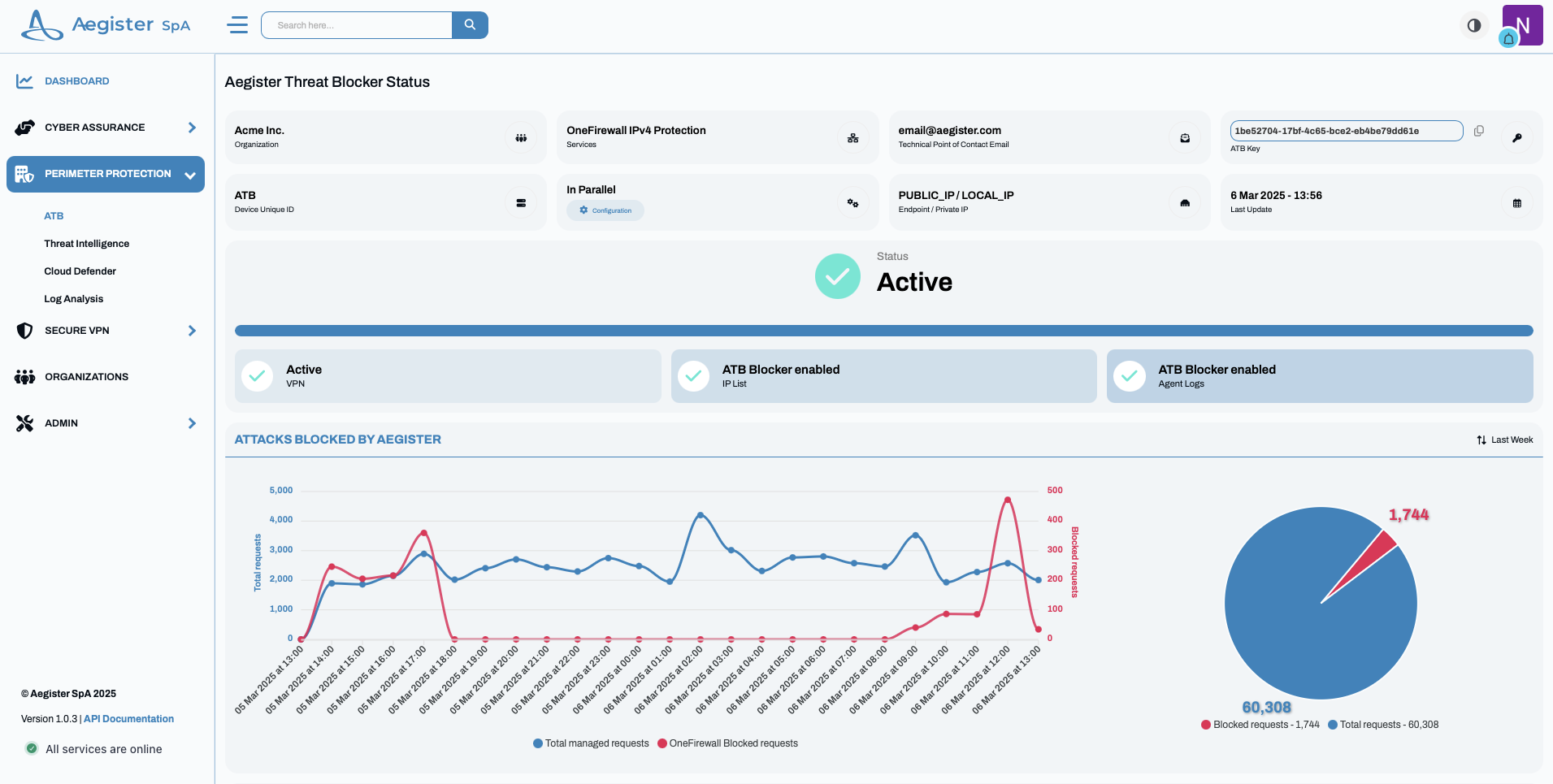
-
Verification Call:
If any issues arise, schedule a call with one of our experts to verify the device’s functionality and its connection with app.aegister.com.
4. Final Steps for Parallel Connection (Generic Firewall)
Follow these steps:-
Access the Firewall Management Interface:
Log in to your firewall’s management interface via its IP address or dedicated hostname using your administrator credentials. -
Connectivity Check:
- Ensure that the ATB device is properly connected to the network and is reachable.
- The IP feed is available at:
Use this URL to verify that the IP blacklist is being correctly downloaded.
-
Security Rules Configuration:
- Create or modify firewall rules to block traffic to or from the IPs listed in the blacklist.
- Typically, you will need at least two rules: one for inbound traffic and one for outbound traffic, setting the action to “Deny” or “Block”.
- Remember to share the rule names with the Aegister team
-
Advanced Settings and Connection Security:
- If your firewall supports automatic updates of the blacklist, configure it for periodic refreshes.
- For a secure (HTTPS) connection, provide a valid certificate to install on the ATB device, or request that we install a self-signed certificate.
-
Logging and Monitoring Configuration:
- Enable logging to monitor events related to your firewall rules.
- Configure log mirroring on UDP port 514 as supported by your firewall to ensure unwanted traffic is blocked.
-
Final Verification and Functionality Test:
- After configuration, download the blacklist again to confirm that it’s up-to-date and that a green check mark (or equivalent indicator) is visible.
- Perform connectivity tests to ensure the blocking rules are active.
-
Documentation and Support:
- If you experience any issues, contact our support team for further assistance.
4.b Final Steps for Parallel Connection (Firewall: Fortigate)
If you are connecting ATB in parallel to an existing Fortigate firewall, follow these steps:-
Access the Fortigate Management Interface:
Log in to your Fortigate firewall’s control panel. -
Create the Security Fabric Object:
- Create a Security Fabric object named “Aegister_Blacklist”.
- Use the link:
Verify that the status shows as “green” and that the list is downloaded correctly.
-
Firewall Policy Rules Configuration:
- Rule 1:
- From: Any
- To: Aegister_Blacklist
- Assign a high rule ID and set the action to Deny.
- Rule 2:
- From: Aegister_Blacklist
- To: Any
- Also configure this rule in Deny mode with a high rule ID.
- Rule 1:
-
Enable Logging:
Activate logging on UDP port 514 to monitor events related to these rules. -
Note for Fortigate:
To ensure connection security, you must install a certificate on the ATB device, as Fortigate accepts only HTTPS connections for Security Fabric objects. Additionally, specify the full filenameblacklist.txtinstead of the default/blacklist.
4.c Final Steps for Parallel Connection (Firewall: SonicWall)
If your environment uses a SonicWall firewall, follow these steps based on the manufacturer’s guide:-
Access the SonicWall Management Interface
Log in to your SonicWall firewall’s control panel. -
Navigate to the Botnet Filtering Section
Go to the Botnet Filtering and Firewall Access Rules section. For additional details, refer to the official guide: How to Configure Botnet Filtering with Firewall Access Rules. -
Configure the Botnet Filter URL
Set the Botnet Filter URL to:Replace<LOCAL_ATB_IP>with the local IP address found in your firewall or in the Aegister Cyber Console – ATB.Note: Once the rules are applied, inform the Aegister team of the Firewall Rule names used.
-
Set Object Limit (Aegister Team)
In the Cyber Console under the ATB section, click Configuration and ensure themaximum_rulesfield is set to: - Verify the Configuration After completing the configuration, verify that the botnet filter correctly downloads the IPs and shows a green checkmark ✅ indicating the blacklist is properly updated.
-
Enable Log Mirroring and Traffic Monitoring
Configure traffic mirroring from WAN to LAN to<LOCAL_ATB_IP>:514 (UDP) on the ATB device. Raw logs are automatically sent to the Aegister Cyber Console. If logs are not displayed, the Aegister team will promptly investigate and correct any parsing issues. For more information on setting up Packet Mirroring on SonicWall devices, refer to the SonicOS documentation. Optional: Log Mirroring is an optional feature that can be enabled at the client’s discretion. It allows sending Syslog traffic from the firewall to the Aegister dashboard, which stores the last 10 million events and provides real-time visual and tabular traffic analytics. These logs focus on both inbound and outbound IPs blocked by our Threat Intelligence system.

