How Aegister Cloud Defender Works
Aegister Cloud Defender secures web applications by analyzing inbound traffic in real time. The process unfolds in several key stages: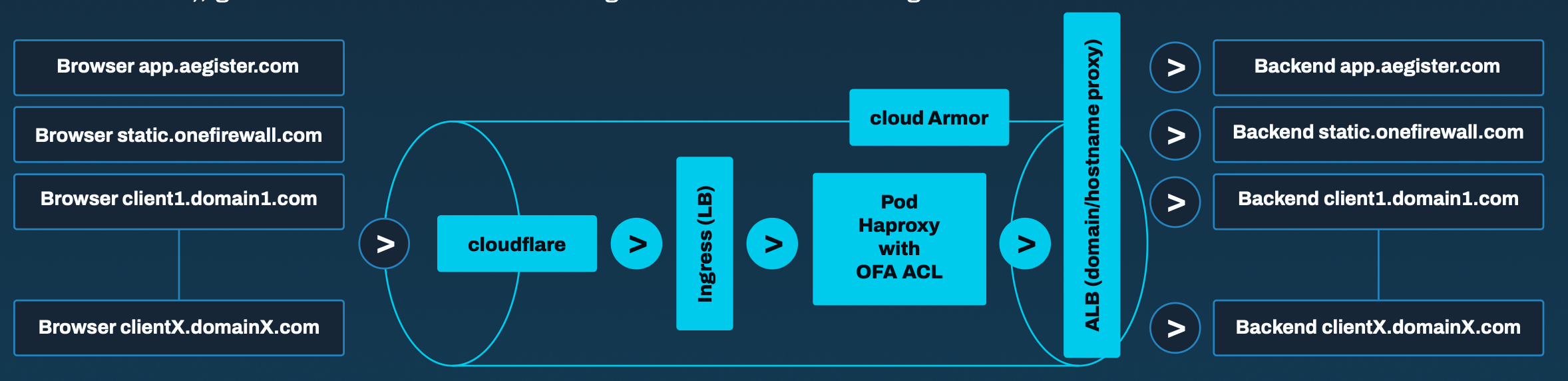
Connection and Integration
- The domain secure.aegister.com connects to Cloud Defender via the Cloud_External_IP_Address.
- The system combines Cloud WAF and OneFirewall Threat Prevention solutions, delivering multi-layered protection against threats.
Request Handling
- When a client sends a request, for example to client1.domain1.com:
- client1.domain1.com is set up as a CNAME for secure.aegister.com.
- The request includes critical details, such as the originating IP address and the X-Forwarded-For header, which trace the traffic’s path.
Traffic Analysis
- Client traffic flows through Cloud Defender (depicted as the “blue tunnel” in the diagram) where it undergoes:
- Threat Intelligence Analysis: Continuously updated WAF rules evaluate the risk associated with each request.
- Traffic Evaluation: Additional queries to client domains or hostnames verify the traffic’s origin and authenticity.
Decision and Action
- Based on the analysis:
- If the traffic is deemed safe, access is granted to the endpoint associated with client1.domain1.com.
- If a high risk level or a malicious IP is detected, the system automatically blocks the request, denying access.

